The Digital Gatekeeper in Healthcare: A Closer Look at Security Verification
In today’s rapidly evolving digital healthcare landscape, security verification is becoming a super important element of protecting sensitive patient data and ensuring that online interactions are genuine. Many platforms have started employing measures that might seem off-putting at first glance, such as the seemingly simple instruction to “press and hold the button until it turns completely green.” On the surface, such measures might appear like little pieces of a complicated process, but when we take a closer look, we find that they are loaded with issues that demand our attention and a balanced perspective.
While many users might find the idea of waiting for a security check a bit nerve-racking, it is essential to understand the hidden complexities behind these digital procedures. In this editorial, we will poke around the pressing need for security verification in healthcare portals and explore why such measures, though sometimes overwhelming in their execution, serve a super important purpose in our modern digital society.
Ensuring Genuine User Interaction in a Digital Healthcare Environment
The digital world, particularly in healthcare, is rife with tricky parts that include both the fine points of data management and the subtle details of online user interactions. Verification processes, such as the instruction to “press and hold,” are fostered by the intention to authenticate that the user interacting with the portal is indeed human. This practice is not simply a quirk of digital systems but a deliberate decision made to reduce automated fraud and misuse of resources.
When we look at this security measure from a broader perspective, we see that it is designed to help steer through a web of issues that range from cyber threats to the overall trustworthiness of digital systems. Instead of viewing these prompts as mere inconveniences, it is essential to recognize the role they play in safeguarding our most sensitive and critical health data.
Healthcare institutions depend on accurate and genuine interactions. Without effective verification, there is a risk that automated systems or malicious entities might infiltrate the system, causing troubled scenarios for patient care and data integrity. Thus, the seemingly simple instruction to “press and hold” is actually the tip of an iceberg full of subtle safety checks that protect critical health information.
Understanding the Button: A Symbol of Trust
The directive “press and hold the button until it turns completely green” is more than just a call to action—it represents a modern solution to a tangled set of challenges that extend beyond healthcare. For digital platforms, including those within the realm of modern medicine and alternative healing practices, such interactive security features convey multiple layers of meaning:
- Verification in Real Time: The process instantly confirms that an individual is physically present and actively engaging with the system, adding an extra layer of protection against robotic or scripted interference.
- Building Trust: By demonstrating a commitment to transparency and robust security measures, healthcare platforms send a reassuring message to users about the integrity and safety of their operations.
- User Engagement: The interactive nature of this process transforms what might otherwise be a passive login step into an engagement opportunity that can reinforce the brand’s assurance in protecting patient data.
In this light, the button that turns green is not a mere technical gimmick—it is a symbol of a system working hard to ensure that interactions are secure and genuine. It pushes the boundaries of simple user interaction into the realm of integrated digital safety.
The Role of Digital Verification in Protecting Health Data
In an era where digital health records and telemedicine consultations are becoming the norm, the need to ensure that every access point is protected has never been more critical. Although these procedures might come across as intimidating, they are implemented to manage and mitigate risks. Let’s take a closer look at some of the small distinctions in digital verification systems that underline their importance:
- Reduction of Cyber Attacks: Automated bots or harmful individuals might try to exploit vulnerable entry points. By confirming a user’s authenticity, these mechanisms help blunt the edge of potential attacks.
- Safeguarding Sensitive Information: Healthcare data is among the most sensitive information, and ensuring that it isn’t accessed by unauthorized parties is a super important responsibility. This necessity drives the implementation of robust verification checks.
- Upholding Patient Trust: Patients who know that a secure verification process is in place are more likely to trust the digital healthcare platforms they interact with. Trust is built upon assurance and demonstrating that every measure is taken to protect personal data.
Yet, for many users, these security measures present little twists that require patience and understanding. The requirement to hover a finger over a button may seem like an off-putting extra step, but when we consider the potential consequences of compromised data, the benefit becomes clear.
Potential Downsides and User Frustration
While the verification process is designed with the best interests of the user in mind, it is not without its challenges. Some may see these processes as nerve-racking or overly complicated pieces that add layers of inconvenience to an already crowded digital space. Let’s break down some of the typical frustrations:
- Time Delays: Any delay in accessing urgent health-related information is seen as an additional hurdle, especially when immediate medical attention is needed.
- User Accessibility: Not all users possess the same level of digital literacy. The extra steps and instructions might be confusing bits for those less familiar with technology.
- Perception of Distrust: For some, being forced to prove their humanity can feel like the system does not trust its users. This can add to the tension and make the user experience less straightforward.
It is crucial to recognize that these annoyances are not borne out of an intent to frustrate but rather from a need to address a world that is full of problems when it comes to cyber security. As patients and users become more familiar with technology over time, these processes might be seen as necessary evils that protect the greater good.
The Intersection of Healthcare and Cybersecurity: A Modern Perspective
Modern medicine and provider networks are no strangers to the trickier parts of data handling and the tangled issues that come with the digital age. With the rise of telemedicine, wearable health devices, and online consultations, the management of health data has become a super important concern for medical institutions and patients alike.
Cybersecurity in healthcare involves ensuring that personal and sensitive medical records remain private and intact. Every verification check—whether it is as simple as pressing and holding a button or undergoing multi-factor authentication—plays a critical role in protecting these records from falling into the wrong hands. The security process in digital healthcare is a fine balance between user convenience and robust protection, which requires deep collaboration between technology experts and medical professionals.
Healthcare Data Breach Scenarios and Their Aftermath
Data breaches can have dire consequences, not just in terms of stolen identities but also in the realm of medical information. Consider the following table that outlines some common scenarios and their impacts:
| Scenario | Impact | Recommended Action |
|---|---|---|
| Unauthorized access to patient records | Compromised privacy, potential misuse of medical information | Immediate account lockdown and multi-factor authentication implementation |
| Ransomware attacks on healthcare systems | Service disruptions, potential data loss | Regular data backups, security awareness training |
| Phishing scams targeting healthcare staff | Unauthorized network access, threat to patient safety | Employee education and robust email filtering systems |
This table is just a snapshot of the spectrum of potential threats that digital health systems encounter daily. Every measure, from simple visual interactions like a green button to complex backend algorithms, is designed to prevent these dangerous scenarios from becoming a reality.
Balancing User Experience with Robust Security Measures
Healthcare digital platforms are constantly trying to find a path that carefully respects both the demands of robust security and the need for a user-friendly experience. The instruction to “press and hold” acts as an example of how even minor, interactive procedures can help bridge the gap between safety protocols and a seamless digital journey.
It is a bit like walking a tightrope where any slight misstep could lead to user frustration or, conversely, a security compromise. Here are some key points on managing this balance:
- User-Centric Communiques: Clear, friendly instructions that guide the user step by step help in reducing the intimidating feel of these measures.
- Simplified Processes: Streamlining the interactions without unnecessary complications ensures that users are not bogged down by confusing bits while still maintaining strong security checks.
- Feedback Mechanisms: Allowing users to report any issues they face when interacting with these processes helps continually refine and improve the overall experience.
With thoughtful design and the input of both cybersecurity experts and healthcare professionals, platforms can make these essential verification steps feel less like a hurdle and more like an integral part of a secure system. Ultimately, this balance enables users to feel confident that the platform not only protects their sensitive health data but also values their time and convenience.
Design Innovations in Digital Health Verification
Recent innovations in digital design have seen several creative approaches to what might have been considered nerve-racking security procedures. For instance, some healthcare apps incorporate animated cues or progress indicators, which help reduce the intimidating nature of waiting for a button to change color. Users can see that the system is working in real time—a small twist that reassures them even as they are momentarily delayed.
Other digital platforms have taken a user-feedback loop to a whole new level by integrating tutorials or simplified language, where the system explains why such a check is essential. This clear communication helps align user expectations with the necessary security protocols, ensuring that the process is as transparent as possible.
The Broader Implications of Security Verification on Public Health
As healthcare moves further into the digital age, the methods by which we secure patient information become a reflection of our commitment to public health. The verification process, including seemingly trivial steps like holding down a button until it changes color, acts as a microcosm of the extensive cybersecurity measures behind the scenes.
Public trust in digital healthcare systems is built upon a foundation of consistent and reliable security practices. When patients are aware that their private health details are guarded by multiple layers of verification, they are more likely to embrace telemedicine and other online health services. This relationship is particularly significant when accessing sensitive treatments, alternative therapies, or even nutritional advice—domains where the personal nuances of one’s health require super important confidentiality.
Moreover, transparent security procedures enhance overall user satisfaction. Patients who know why certain steps are necessary are less likely to feel overwhelmed by the process. They recognize that every small detail, no matter how complicated it might seem, is part of a bigger strategy designed to protect their well-being.
Community Engagement and Security Literacy
One of the additional benefits of clear and interactive security protocols is the opportunity for educational engagement. Healthcare digital platforms have the power to influence public understanding of cybersecurity. This means dedicating efforts to explain, in simple terms, why steps such as “press and hold” are implemented can demystify the process for the average user.
Some effective ways to promote this security literacy include:
- Online Tutorials: Short videos or interactive guides that walk users through the verification process, explaining every twist and turn of the procedure.
- FAQ Sections: Detailed frequently asked questions that address common concerns and provide plain-language answers about why these measures are necessary.
- Community Webinars: Regular sessions where cybersecurity and healthcare experts discuss the safety features of the digital platform, fostering a culture of transparency.
By incorporating these educational tools, digital healthcare providers not only secure access but also empower their users, helping them to get around the technical trickier parts with confidence and understanding. In this way, the community becomes an active partner in maintaining the security of their health data.
Technological Advancements and Future Directions in Health Verification
Looking ahead, the digital verification processes we see today are likely to evolve as technology continues to advance. Emerging technologies such as biometric authentication, artificial intelligence, and blockchain are already beginning to shape the future of secure online interactions.
These advancements promise to streamline security while addressing many of the confusing bits and tangled issues that users currently face. For example, biometric verification—whether through fingerprint scanning, facial recognition, or even voice recognition—offers a more seamless way to confirm a user’s identity without the manual act of holding down a button.
Similarly, the integration of AI-powered systems can help manage unusual access patterns or verify human interaction more subtly. Rather than relying solely on visual cues like a button turning green, these systems can continuously learn and adapt to improve the user experience while maintaining super important security.
Anticipated Innovations in Cybersecurity for Healthcare
The table below provides a snapshot of some anticipated trends and future innovations in digital verification for healthcare:
| Emerging Technology | Potential Benefit | Challenge Addressed |
|---|---|---|
| Biometric Authentication | Smooth user verification using personal physical features | Reduces reliance on manual interactions like pressing a button |
| Artificial Intelligence | Dynamic monitoring and adaptive security checks | Manages unusual behavior without intrusive measures |
| Blockchain | Creates an immutable ledger of user interactions | Ensures integrity and accountability of health data transactions |
These future directions are a testament to the ongoing need to balance ease of use with strong security protocols. With these tools, the industry is working through the challenges of digital verification while making a path toward an increasingly secure digital healthcare environment.
Integrating Alternative Medicine and Nutritional Platforms into the Cybersecurity Framework
The healthcare domain is not limited to conventional medicine. With the growing popularity of alternative therapies, nutritional guidance, and holistic wellness platforms, the pressure to implement effective security measures expands. Users turning to these alternative areas demand the same super important standards of data protection as conventional healthcare, despite the different types of information involved.
Alternative medicine platforms often handle very personal information—from dietary preferences to details about alternative treatment regimens. In this context, ensuring that every user is who they claim to be is essential. The security process, even if it includes nerve-racking steps like holding a button until it turns green, becomes a common thread that unifies diverse areas of health under one umbrella of safety and trust.
Furthermore, nutritional platforms that offer personalized meal plans or track dietary habits store insights that can directly impact one’s health outcomes. Therefore, the digital security measures deployed across these platforms are critical not only to secure data but to enhance patient trust and adherence to recommended health regimens.
Collaborative Approaches Between Conventional and Alternative Health Sectors
To find a path that bridges addressing the digital skeptical tendencies in both conventional and alternative healthcare sectors, it is important that there be a cooperative approach. Some important points include:
- Unified Security Standards: Developing and implementing consistent security protocols across various platforms can reduce user confusion and ensure data protection is uniform, whether the source is a hospital portal or a holistic health app.
- Cross-Sector Education: Sharing best practices in secure verification procedures can foster mutual understanding between conventional medicine providers and alternative therapy platforms.
- User-Centered Design: Both sectors would benefit from intuitive designs and clear instructions that help users get into the verification process without feeling overwhelmed.
Ultimately, a collaborative model where technology providers and healthcare professionals work together to ensure secure, yet user-friendly, verification processes will benefit everyone—patients, providers, and digital health innovators alike.
Conclusion: A Balanced Future for Digital Healthcare Security
The directive to “press and hold the button until it turns completely green” might appear as a minor instruction in the vast digital healthcare landscape. However, when we look at the broader picture, it becomes clear that such measures are crafted to address a slew of tricky parts and tangled issues. From ensuring genuine user interaction to protecting sensitive patient data, these security verification steps are essential components that help build trust and safety in the digital realm.
While users may sometimes feel that these methods add to the overwhelming nature of navigating online health platforms, it is important to remember that each small detail is part of a larger strategy designed to fend off cyber threats and provide a secure environment for all. Through continued innovation, user education, and collaborative efforts between technology and healthcare professionals, the seemingly intimidating nature of these processes can be transformed into an engaging, reassuring facet of modern digital healthcare.
The future of healthcare will undoubtedly involve more sophisticated tools that streamline verification without sacrificing security. Biometric systems, AI-driven authentication, and blockchain technology represent just a few of the exciting avenues being explored. As we continue to work through the confusing bits and hidden complexities of digital verification, one truth remains constant: patient privacy and data integrity are super important and must be preserved at all costs.
In our digital age, every press and hold action is a small, yet significant, step toward a world where every healthcare interaction is protected and every user’s data is safeguarded. While the process might seem a bit off-putting on the surface, it ultimately represents the dedication and commitment of healthcare providers to ensure a safe digital future—a future where trust, transparency, and secure interactions stand as the backbone of modern medicine.
Ultimately, as technological advancements continue to evolve our methods for confirming genuine interactions, the healthcare industry will remain at the forefront of integrating security and convenience. The conversation about digital safety is ongoing, and every verified click, every green-lit button, contributes to a robust, secure, and user-friendly ecosystem that serves the best interests of patient care and public health.
As stakeholders in the world of healthcare—be it through traditional channels, alternative medicine, or nutritional guidance—it is our responsibility to ensure that all pieces of our digital world work together harmoniously. By taking a closer look at every step, from holding a button to embracing new technological solutions, we are not only protecting our present but setting the stage for a secure, confident, and trustworthy digital healthcare future.
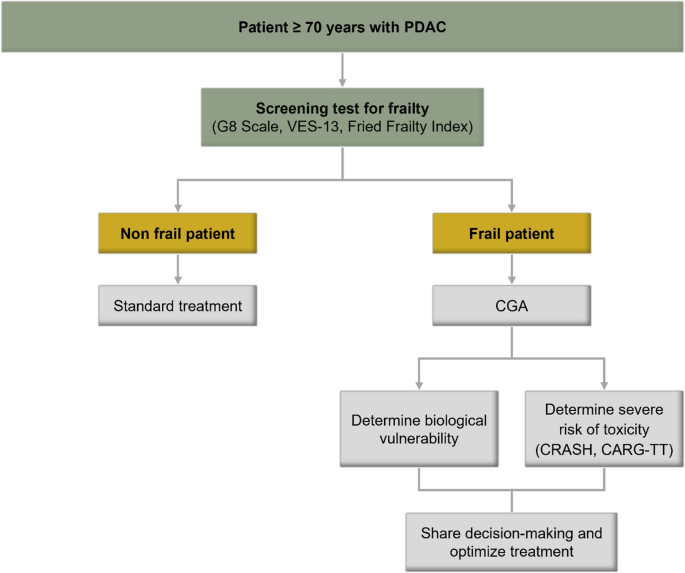
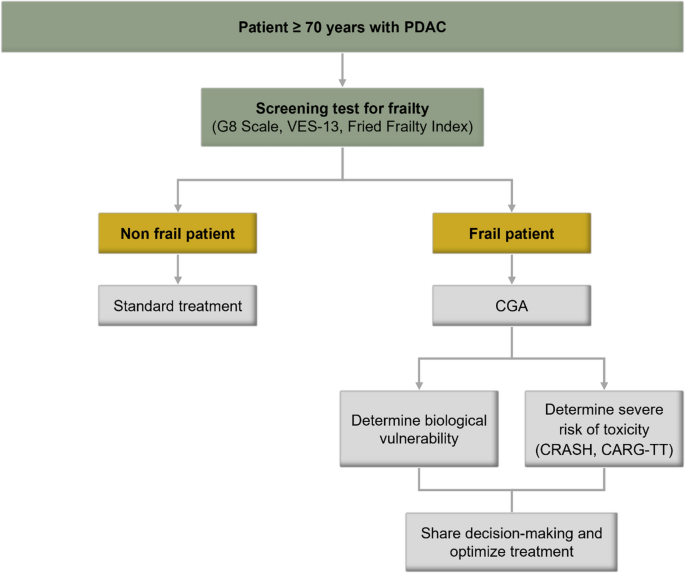
Originally Post From https://medicalxpress.com/news/2025-11-factoring-frailty-age-pancreatic-cancer.html
Read more about this topic at
Human Verification Required: Copy & Paste Your Malware …
Fake Human Verification Prompt Delivers Infostealers