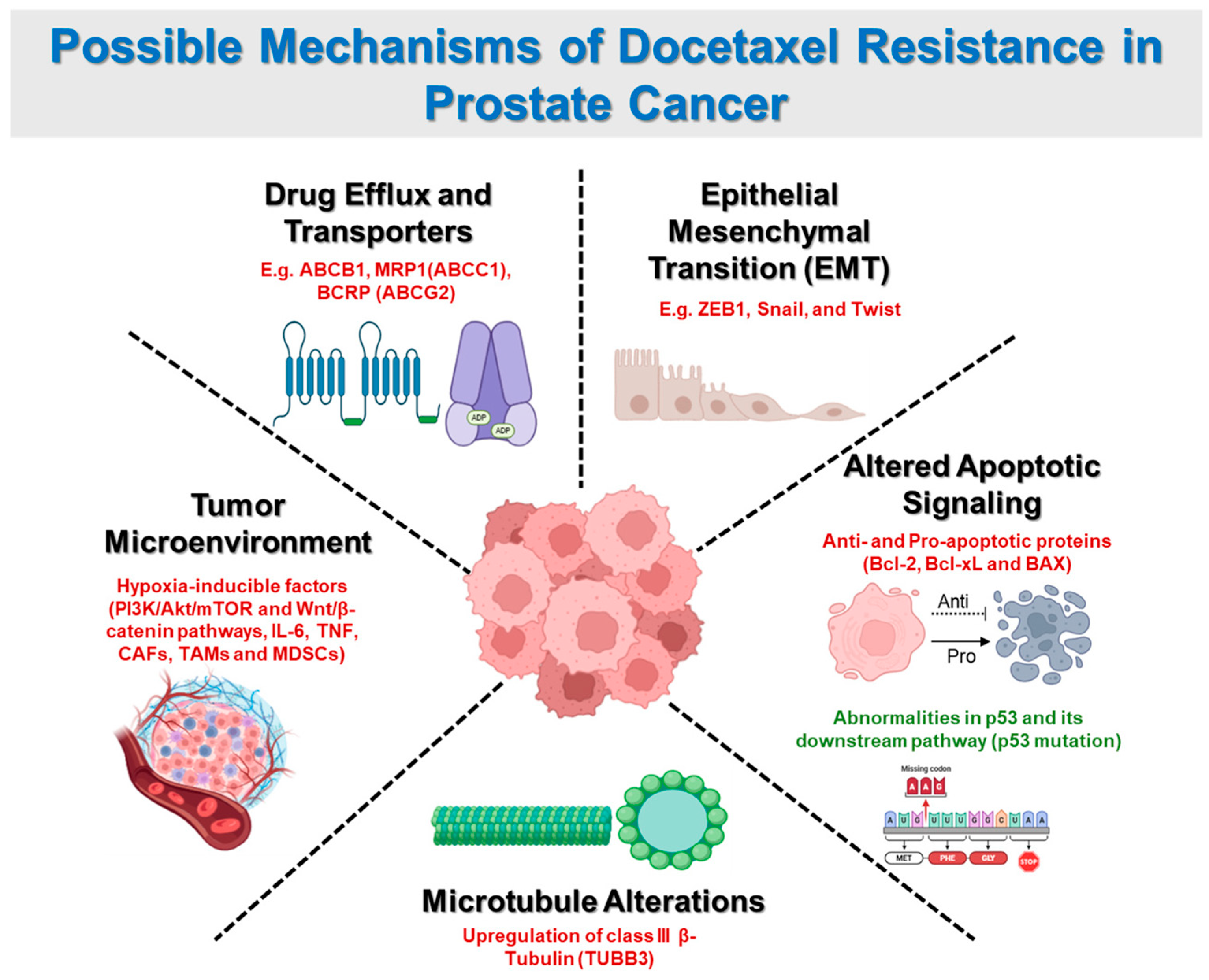
The Digital Age of Healthcare: Balancing User Trust and Online Security
In today’s fast-changing world of modern medicine and alternative health information, online healthcare portals have become a cornerstone for both patients and professionals alike. With the increasing reliance on digital platforms to access everything from clinical research to holistic solutions, it is essential that these websites incorporate robust security measures. As the user experience evolves, many healthcare websites now require visitors to confirm they are human, employing systems that check the security of a connection before allowing access.
This verification process, typically powered by services such as Cloudflare, plays a critical role in safeguarding sensitive medical data and ensuring that web traffic is genuine. While these measures may feel intimidating to the average visitor, they are a necessary part of building trust and ensuring comprehensive online safety. Healthcare websites must figure a path through a shifting landscape where every click might expose tangled issues or frightening tactics by cybercriminals.
The Essentials of Digital Verification on Healthcare Portals
One of the key aspects of modern online security is the quick, automatic process that verifies if visitors are legitimate users. This simple, yet effective procedure not only streamlines the user experience but also protects the integrity of the platform. Many healthcare websites employ a brief waiting period during which the system checks the connection’s security credentials. If the verification is successful, access is granted, and visitors continue on their journey toward discovering valuable health information.
This procedure is super important because it helps screen out automated threats, such as malicious bots that can lead to data breaches or misinformation spread. Even though these security checks might seem like a minor inconvenience, they serve as a first line of defense against many of the little problems that can arise from an unprotected digital environment.
Understanding the Verification Process
When you try to access a secure healthcare site, you might notice a message stating, “Verifying you are human. This may take a few seconds.” This message is part of a process designed to filter out automated traffic. During this time, the website is busy reviewing the security of your connection before proceeding further, ensuring that only genuine users can access confidential content.
Once verification is successful, the system swiftly moves on to load the rest of the site. By incorporating these security features, healthcare providers can protect both sensitive patient data and essential health information, making these measures a must-have in the digital age.
Cloudflare and Its Role in Healthcare Security
Cloudflare is one of the major players behind the scenes, powering the performance and security of millions of websites, including those in the healthcare sector. This service provides a variety of benefits that are crucial for ensuring the smooth operation of online medical information platforms.
How Cloudflare Keeps Healthcare Platforms Secure
Cloudflare acts as a proxy between the user’s computer and the healthcare site, filtering out bad traffic and ensuring that only credible, human users get through. It employs a series of filtering techniques and real-time monitoring to detect and block suspicious activities. In doing so, Cloudflare protects websites from typical automated attacks and helps prevent the exposure of sensitive information.
The online obligation to secure patient data is not to be taken lightly. By leaning on the services provided by Cloudflare, healthcare portals can reduce the risk of adverse incidents and protect both the institution’s reputation and the personal information of millions of users.
The Hidden Complexities of Cloudflare Integration
Implementing Cloudflare’s security measures involves getting into layers of verification that are full of problems and tangled issues. Many administrators must figure a path through retrieving the right settings and calibrating the level of protection needed. Some challenges include:
- Fine-tuning security to prevent false positives that might block genuine users
- Balancing performance with security so as not to overwhelm the site
- Managing user expectations when a waiting period is involved
- Ensuring seamless integration with existing healthcare data systems
Despite these tricky parts, the overall benefit is clear. Healthcare websites can benefit from a secure environment that manages to ward off potential threats while offering relatively smooth access for verified users.
Redirecting Focus: Trust and User Experience in Healthcare
Beyond the technical details, the implementation of digital verification processes has broader implications for trust and user experience. The manner in which security measures are communicated and enforced has a direct impact on how users perceive a website. A verified connection not only reassures visitors that their sensitive health information is protected but also builds confidence in the reliability of the content being provided.
Managing Your Way Through the Patient Experience
Patients looking for reliable healthcare information, ranging from modern medical research to holistic approaches, are more likely to trust websites that take online security seriously. However, the process of managing your way to secure access is also navigable with a few key considerations:
- Clear communication: Websites should inform users about why they may experience a brief delay during the verification process.
- User-friendly design: An intuitive interface can significantly reduce any potential frustration associated with security checks.
- Reliable support: In cases where users encounter issues, having an easily accessible help resource is indispensable.
A balance must be struck between stringent security protocols and a fast, easy-to-navigate user experience. Healthcare professionals and IT specialists alike agree that a well-integrated system is essential for maintaining the delicate balance between accessibility and the protection of sensitive data.
Digital Security and Its Impact on Patient Data Privacy
The protection of patient information is a super important aspect of maintaining trust in any healthcare system. With the increasing digitization of medical records and telemedicine platforms, it has become critically important to keep privacy breaches at bay. The verification methods employed at the outset of the user’s visit not only act as a gatekeeper but also help shield confidential data from potential cyber-attacks.
Ensuring Data Safety Through Robust Verification
Every time a user is asked to confirm they are human, a series of security protocols are set in motion. These can include:
- IP address verification to ensure connections are originating from recognized sources
- Behavioral analysis to detect unusual patterns or potential automated bots
- Encryption protocols to safeguard the transmission of data between the user and the website
Each of these checks serves as a small shield against cyber threats. Although the fine points of these security layers might appear overwhelming, in truth, they are designed to work quietly in the background, providing continuous protection without major interference in daily user activities.
Potential Challenges in Data Management
Despite the strong protective measures, the challenge of ensuring data safety is not without its tricky parts and complicated pieces. Among the issues that healthcare IT specialists face are:
| Challenge | Impact | Suggested Approach |
|---|---|---|
| User Experience Delays | Patients might feel off-putted by any delays during verification | Streamline processes and provide clear, friendly notifications |
| Integration Hiccups | Sensitive systems might conflict with new security tools | Conduct thorough testing and use compatible solutions |
| False Positives in Security Checks | Legitimate visitors may get blocked accidentally | Optimize algorithms and allow for manual overrides |
Addressing these challenges requires collaboration between IT teams, healthcare professionals, and security experts. Solutions must be flexible enough to adjust to the user’s needs while robust enough to fend off any potential threats.
Integrating Modern Medicine with Cybersecurity Practices
Modern medicine is always evolving, with breakthroughs and cutting-edge treatments emerging at a rapid pace. In parallel, the methods used to protect sensitive healthcare data must also evolve. Just as new medical therapies are being discovered and refined, the digital tools used to secure online platforms continue to become more sophisticated.
Steps to Bolster Cybersecurity in Healthcare Applications
Healthcare administrators should consider taking a proactive role in protecting their digital assets by implementing a comprehensive cybersecurity strategy. Some of the key steps include:
- Regular audits of security infrastructure to detect and address small distinctions in potential vulnerabilities
- Investing in advanced verification methods that balance security with user convenience
- Conducting training sessions for staff on the latest trends in cybersecurity
- Maintaining up-to-date software and systems to minimize the risk of exploitation
By taking these steps, healthcare providers can remain several steps ahead of those who might misuse data, ensuring that their digital spaces remain secure yet accessible.
Alternative Medicine and Its Place in the Digital Security Ecosystem
While modern medicine often takes center stage, the realm of alternative medicine has grown significantly and increasingly relies on digital platforms for dissemination and discussion. Just like conventional medicine websites, these platforms also need to implement robust security checks to maintain credibility and protect user discussions and shared experiences.
Alternative practices—ranging from herbal remedies to mind-body techniques—often attract a diverse audience seeking both traditional and unconventional wisdom. Because online forums that discuss alternative health approaches are also subject to misinformation and potential hacks, they benefit immensely from a layered security approach. The process of verifying users helps ensure that the advice, testimonials, and health tips shared online are coming from genuine sources.
Evaluating the Pros and Cons of Automated Verification Systems
The introduction of automated verification processes in online healthcare platforms has sparked a lot of debate among professionals. While some see these methods as the key to unlocking a safer digital environment, others are wary of potential drawbacks that might arise from reliance on automated systems.
Benefits of Automated Verification in Healthcare
There are several clear advantages to the use of automated systems in verifying users on healthcare sites:
- Enhanced Security: Automated systems can detect and block harmful bots and malicious actors before any damage is done.
- Efficient Gatekeeping: With rapid verification checks, legitimate users can access essential health information with minimal delay.
- Data Integrity Examples: Automation helps ensure that the data being accessed or shared is less likely to be tampered with.
- Scalability: As the volume of users increases, automated systems adapt, offering continuous protection without exhausting human resources.
These benefits illustrate why many experts believe that automatic verification forms are a cornerstone of modern digital security, especially within the sensitive realm of healthcare.
Concerns and Limitations
Despite its advantages, there are some tricky parts associated with automated verification systems:
- User Frustration: Some visitors may find the waiting period nerve-racking, particularly if they are in urgent need of information.
- Overblocking: In some cases, overly sensitive systems might mistakenly block valid users, causing disruptions.
- Privacy Considerations: While these systems are designed to protect data, there is always an ongoing debate regarding the balance between surveillance and privacy.
- Technical Glitches: Like any technological solution, automated checks can experience issues that momentarily interrupt access.
These challenges highlight the importance of ongoing assessments to ensure that security measures remain effective yet unobtrusive. A collaborative approach, where IT experts, healthcare professionals, and patient advocates work together, is essential to address these small distinctions and complicated pieces.
Striking a Balance: Patient Experience Versus Security Overhead
The balance between ensuring tight security and offering a smooth, user-friendly experience is one of the most talked-about issues among healthcare providers. Patients and professionals alike benefit when online portals manage to secure sensitive data without making the process overwhelming or overly intimidating.
Key Strategies for a Seamless Experience
To achieve this balance, healthcare websites can employ several effective strategies:
- Straightforward Communication: Clearly explain to users why security checks are necessary and how they protect personal data.
- Optimized Verification Times: Invest in technologies that speed up the verification process so that delays are minimal.
- User-Centric Design: Design interfaces that are both intuitive and informative, reducing confusion during the verification.
- Responsive Support: Offer immediate help through FAQs, live chats, or support lines for those who encounter issues during access.
Adopting such strategies enables users to work their way through the verification process with a clear understanding of the benefits, helping to mitigate any feelings of unease that may arise from these necessary security measures.
Real-World Examples and Case Studies
Many healthcare institutions have successfully implemented robust verification systems that both maintain security and enhance user experience. Consider the following examples, which illustrate various strategies used across the digital healthcare spectrum:
| Institution | Strategy | Outcome |
|---|---|---|
| Leading Cancer Research Center | Integrated Cloudflare security with rapid site loading | Maintained continuous access with minimal user complaints |
| Telemedicine Startup | User-friendly verification prompts paired with robust encryption | Increased patient trust and reduced false block incidents |
| Alternative Medicine Forum | Dual-layer verification combining human oversight and automation | Optimized community engagement without compromising privacy |
These case studies provide insight into how carefully balancing user experience and top-notch security can yield positive outcomes. Each institution had to sort out a unique blend of verification strategies and adopt best practices to protect their digital content effectively.
Preparing for the Future of Digital Healthcare
As healthcare continues its journey into the digital era, the importance of secure online platforms will only grow. The challenges are many, and the path forward involves constant vigilance and adaptation to new threats. It is essential for every healthcare provider—from established hospitals to emerging alternative medicine platforms—to keep a close eye on developments in cybersecurity.
Emerging Trends in Healthcare Cybersecurity
Looking ahead, several emerging trends stand out as instrumental in shaping the future of online healthcare security:
- Artificial Intelligence and Machine Learning: These technologies are being used to monitor traffic patterns in real time, predict potential security risks, and adjust verification parameters on the fly.
- Behavioral Biometrics: By analyzing unique user behavior patterns, newer systems can more accurately distinguish between genuine users and automated threats.
- Decentralized Data Storage: With advancements in blockchain and decentralized systems, there is potential for enhanced security and transparency in the management of sensitive health records.
- Privacy-Enhancing Technologies: New methods that help to minimize the data footprint while still providing strong verification protocols are on the rise, further building trust among users concerned about data privacy.
These advancements represent both opportunities and challenges. They are super important because they promise to bolster security measures further while potentially streamlining the user experience. However, it remains crucial for developers and healthcare providers to stay engaged with the latest findings, adopt flexible strategies, and be prepared to figure a path through unforeseen challenges.
Steering Through a Future Full of Digital Tangles and Hidden Details
In an environment that is loaded with issues and little twists in technology, the continual evolution of cybersecurity measures is essential. Healthcare providers will need to get around not only the technical obstacles but also the subtle details involved in striking the right balance between robust security and ease of access for patients seeking guidance and care.
For instance, the future may demand the integration of more personalized user experiences with enhanced security protocols—transforming the generic verification form into something that adapts based on a user’s behavior and history. This not only improves protection but also helps reduce needless delays and frustration during critical healthcare interactions.
Conclusion: A Call for Collaborative Innovation in Healthcare Security
The integration of advanced digital verification techniques on healthcare websites is more than just a technical requirement—it is a statement of commitment to protecting patient data and fostering trust in an era where health information is just a click away. While the process of verifying users and securing connections involves its own set of tricky parts and confusing bits, these efforts are indispensable for ensuring that sensitive information remains safe.
From leveraging the technology of Cloudflare to implementing user-friendly verification protocols, the digital health space is making great strides toward a secure, efficient future. Healthcare professionals, cybersecurity experts, and web administrators must continue to work closely together to sort out the challenges and fine-tune the little details that can make all the difference.
In the grand scheme, each step toward better security contributes to a safer, more informed public. Whether you are a patient seeking medical advice or a professional in the field, understanding and appreciating these digital safeguards can help you feel confident in the information at your fingertips. The process of online verification may add a few extra seconds to your experience, but those seconds are an investment in protecting what matters most—your health and privacy.
As we continue to witness evolving trends in both medicine and digital security, it is clear that collaborative innovation will be the key to navigating the twists and turns of this landscape. With ongoing improvements in technology and the adoption of flexible, user-centered approaches, the future of online healthcare is not only secure but also a model for other sectors where trust and data integrity are on edge every day.
Ultimately, the convergence of modern medicine and digital security represents a forward-thinking approach to the challenges posed by our increasingly virtual world. By taking a closer look at the issues and fine-tuning our security measures, we can ensure that healthcare websites remain safe havens for accurate health information and reliable patient care. It is a nerve-racking task at times, but one that is absolutely critical in our pursuit of a secure digital health ecosystem.
In these times of rapid technological change, the importance of transparent, effective security measures cannot be overstated. Whether you are reading the latest breakthrough in clinical research or exploring alternative health remedies, the trust you place in these digital spaces is what ultimately allows us to build a healthier future—one secure, verified step at a time.
Originally Post From https://www.urotoday.com/trials-in-progress/aspire-trial.html
Read more about this topic at
Cloudflare Turnstile | CAPTCHA Replacement Solution
Stuck on ‘Verifying you are human. This may take a few …
