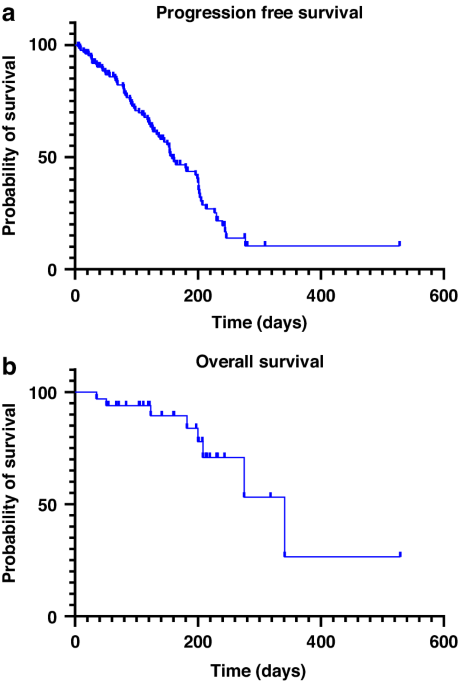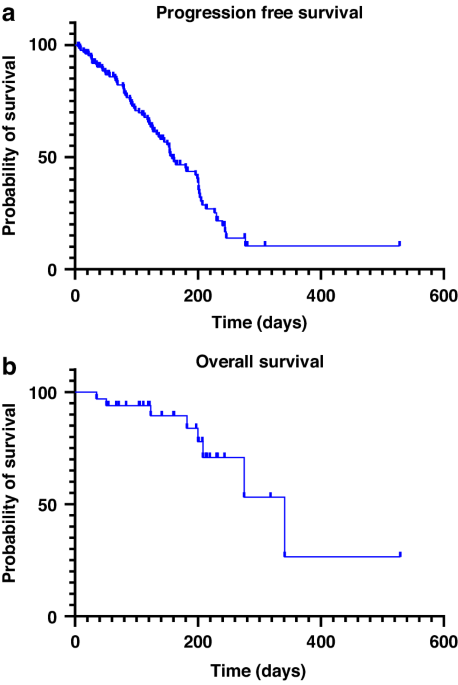
Unmasking the Hidden Complexities of Secure Verification in Online Healthcare Portals
In today’s digital era, where healthcare and technology increasingly intertwine, ensuring the security of online systems is a task that requires both diligence and innovation. As healthcare organizations expand their digital presence—whether through patient portals, electronic health records, or online appointment systems—secure verification mechanisms have become critical. These verification methods are the gatekeepers to patient data and many other services, and they are designed to distinguish humans from automated bots in order to protect sensitive information.
While the message “Please complete security verification” might seem like a simple prompt, it symbolizes a larger commitment to safeguarding personal data. In one notable example, users are instructed to “press and hold the button until it turns completely green,” a directive that might feel both unconventional and, at times, nerve-racking for individuals who are not technologically savvy. This editorial explores the wide-ranging issues involved in designing and implementing secure verification systems on healthcare platforms, discussing their benefits, potential pitfalls, and the ways in which they might evolve to better serve end users.
Why Robust User Verification is Essential in Modern Healthcare
Careful consideration of secure verification methods is more than just a technical issue—it is central to maintaining user trust and protecting critical health data. In an age where cyberattacks and data breaches have become all too common, healthcare providers have embraced multi-step security protocols to ensure that only authorized individuals gain access to sensitive information.
The importance of these measures is underscored by the fact that healthcare data is particularly coveted by cybercriminals. Patients’ personal, diagnostic, and treatment information offer rewards that are both financially and personally damaging if misappropriated. A well-designed verification process offers protection by adding a layer of safety before granting access.
Beyond the defense against external threats, secure verification processes also help manage the delicate user experience. Many patients might find these measures intimidating, especially if they are unfamiliar with the underlying technology. Consequently, a careful balance must be struck between security and usability—a balance that remains one of the trickiest parts in today’s digital healthcare landscape.
Digital Authentication in Healthcare: Balancing Security and Usability
Modern healthcare systems are tasked with an enormous responsibility in terms of data protection. As users log in to access their medical records or schedule appointments, they face verification prompts that require a clear understanding of what is expected. The instruction to “press and hold the button until it turns completely green” is one such example; at first glance, it seems straightforward, but its practical application can require users to deal with several tangled issues.
This approach demonstrates a kind of interactive challenge that not only confirms that the user is human but also seeks to reassure them that the system is functioning properly. Despite its simplicity in instruction, the process can feel somewhat overwhelming for some users, especially if they are already anxious about online security. The fine line between user-friendly design and overly complicated verification methods is drawn in subtle details that can sometimes seem nerve-racking.
Healthcare organizations must take these subtle distinctions into account. By designing verification processes that are both secure and intuitive, providers can ensure that patients do not find these steps off-putting. After all, an efficient and user-friendly process is super important for encouraging regular use of online healthcare services.
Press and Hold: The Button Verification Challenge
The instruction to “press and hold the button” may appear to be a quirky or unusual requirement at first, but it reflects a growing trend in authentication design: the use of interactive tasks to confirm human presence. This method works by engaging the user in a tangible action that is difficult for automated systems to mimic. The visual cue—typically a button that changes color to green when correctly held—is a clear indicator that the verification process has been successfully completed.
Despite the apparent simplicity, this verification challenge is loaded with the following considerations:
- User Interaction: The physical action required assures that an actual person is at the helm rather than a script or automated bot.
- Feedback Mechanism: The color-changing button provides immediate visual feedback, which is an essential part of enhancing trust in the system.
- Ease of Use: While the process appears straightforward, it must be tested extensively across various devices and among different age groups to ensure that it does not inadvertently become a stumbling block.
Moreover, the notion that pressing and holding a button is enough to verify a user’s humanity highlights both the strength and limitations of current security strategies. On one hand, it is a clever workaround to the increasingly sophisticated methods used by cyber attackers. On the other, the simplicity of the method could be seen as a potential flaw if it proves inadequate against advanced automated attacks.
Understanding the Impact on Patient Trust and Engagement
The introduction of verification challenges in healthcare systems does not simply serve a technical purpose; it also plays a key role in building and maintaining patient trust. Users need to feel confident in the security of the platforms they rely on to access their health information. If the process feels overly complicated or intimidating, it may deter some individuals from using these crucial online services.
A straightforward verification process provides several benefits:
- Strengthening Digital Trust: A transparent process that immediately shows a positive result (like a green button) can be reassuring.
- Improving Patient Engagement: When users are not deterred by confusing bits or tortuous steps, they are more likely to continue using online resources.
- Minimizing Frustration: Ensuring that the steps are simple and direct reduces user frustration and helps avoid potential drop-offs.
However, implementing such measures does come with its own set of challenges. The process might seem intimidating to some, and if it is burdened with too many complicated pieces or hidden complexities, patients could become frustrated. Consequently, healthcare providers must continuously assess and refine their verification processes to ensure that they strike the ideal balance between security and ease of use.
Interactive Security: A Closer Look at Button-Based Verification
Security verification in its many forms has evolved significantly over the years. One interactive method that has gained traction in recent times is the use of button-based verification systems. These systems are often designed to confirm that the person interacting with the platform has real-time control and is not a script executing commands in the background.
A deeper look at this kind of interactive security reveals several key aspects:
| Aspect | Advantages | Potential Issues |
|---|---|---|
| User Engagement | Engages the user in an active process; provides immediate feedback. | May be nerve-racking for those unused to interactive designs. |
| Simplicity of Design | Offers a clean and straightforward challenge. | Could oversimplify verification, possibly leaving gaps in security. |
| Real-Time Interaction | Prevents automated scripts from easily bypassing the verification. | May be problematic on devices with slower response times. |
This table underscores the key benefits and challenges associated with button-based verification methods. It is essential to note that while interactive systems such as these have carved a niche in improving security, they must continuously evolve to address the subtle parts and unexpected twists and turns that come with technological advancements.
Overcoming the Intimidation Factor in Digital Healthcare Verification
For many, the digital transition of healthcare services has introduced several intimidating hurdles. The introduction of verification gates, such as the simple “press and hold” challenge, can add to that sense of overwhelm. Particularly for individuals new to digital healthcare systems or those who are less technologically literate, these tasks can appear off-putting.
Let’s take a closer look at some strategies to reduce the overwhelming factor and ensure that digital verification is both accessible and functional:
- Educational Initiatives: Providing clear, concise tutorials and explanatory messages can demystify the process. Short video guides or interactive demos can be invaluable.
- User-Centered Design: Involving patients in the design phase to gather feedback can lead to interfaces that are attuned to user needs, reducing potential confusion.
- Adaptive Interfaces: Creating verification systems that adjust based on the device or the user’s behavior can help ensure that the process is smooth regardless of technical constraints.
By integrating these solutions, digital healthcare providers can work through the tangled issues associated with verification protocols. The aim is to design a system that not only fortifies security but also respects the patient’s journey, ensuring that the experience is as seamless as possible.
Securing Health Information: The Intersection of Modern Medicine and Online Verification
Healthcare is at a crossroads where the integration of modern medicine and digital technology has led to dramatic improvements in patient care—but it has also introduced a series of challenging bits in terms of cybersecurity. The intersection of these fields is laden with both opportunities and risks.
On one side, advanced security verifications such as the “press and hold” method contribute to the overall integrity of digital healthcare systems. On the other, the rapid pace at which technology evolves means that new threats are continually emerging, forcing providers to update and refine their protocols.
Several key areas of focus include:
- Data Privacy: Ensuring patient records remain confidential is super important. Robust verification systems act as the first line of defense against unauthorized access.
- System Resilience: As healthcare systems become increasingly interconnected, even a minor breach can have widespread consequences. Continuous improvements in digital security are essential to minimize risks.
- Patient Empowerment: Allowing patients to access their data with swift, secure methods helps to build confidence in digital solutions, encouraging them to take an active role in their healthcare journey.
The fine details of how these systems work may sometimes seem like complicated pieces, yet they are key to creating a safe environment both for patient data and for the broader digital healthcare ecosystem. Healthcare providers must continue to innovate and adapt by considering alternative security layers that complement the traditional “press and hold” verification.
Exploring Alternatives: Beyond the Traditional Verification Model
While the “press and hold” button verification has proven to be a creative solution, it is by no means the only approach available. With rapid advancements in biometric technology, artificial intelligence, and behavioral analysis, several alternative methods are emerging that could further bolster security within healthcare environments.
Some of these methods include:
- Biometric Verification: Fingerprint scanning, facial recognition, and even voice authentication are being integrated into healthcare portals to provide an additional layer of security. These methods confirm identity based on personal biological traits, adding a tangible barrier against unauthorized access.
- Behavioral Analysis: By analyzing patterns in how a user interacts with a system—including keystroke dynamics and mouse movement—systems can identify anomalies that may indicate automated access attempts.
- Multi-Factor Authentication (MFA): MFA combines multiple forms of verification (such as a password, a fingerprint scan, and a one-time code) to enhance overall security. This layered method is particularly effective in distinguishing between legitimate users and sophisticated attack mechanisms.
Adopting such alternatives or integrating them with existing methods can assist healthcare providers in making their systems even more secure. However, each method comes with its own set of challenges—if not implemented carefully, even advanced systems can introduce new complicated pieces or create additional user barriers. For instance, biometric systems require expensive hardware and must address privacy concerns, while behavioral analysis demands continuous monitoring that some users might find intrusive.
The way forward is not necessarily a single solution but rather a combination of methods that address the hidden complexities of digital security while remaining accessible and practical for everyday use in healthcare settings.
User Experience and the Human Factor in Security Verification
Underlying every verification system is the fundamental need to create an interface that feels natural to users. Whether it is through a simple button that turns green or a sophisticated biometric scan, the human factor in security verification cannot be overlooked. Patients and healthcare providers share a mutual expectation for technology that works reliably without overwhelming the user with confusing bits.
Here are some key considerations in optimizing user experience:
- Clarity and Simplicity: Clear instructions such as “press and hold until the button turns green” can help direct the user’s actions. Keeping the language straightforward avoids adding unnecessary twists and turns in the process.
- Responsive Feedback: Immediate feedback reassures the user that their action has been properly recognized. Visual signals—whether through color changes or animations—are small distinctions that can make a huge difference in enhancing user confidence.
- Accessibility: The process needs to be adaptable for users with disabilities or those with limited technological proficiency. This means designing alternative pathways or assistive features in tandem with the standard verification method.
By taking a patient-centric approach and engaging in regular user testing, developers can figure a path that minimizes the intimidating aspects of security protocols while maintaining super important safeguards for sensitive data.
Case Studies: The Ripple Effect of a Simple Verification Process
Real-world examples highlight how even minor modifications to the verification process can yield significant improvements in both security and overall patient satisfaction. Several healthcare organizations have implemented interactive verification steps with encouraging results:
- A Major Hospital Network: After introducing a button-based verification protocol, the hospital network saw a noticeable decrease in automated bot attacks while receiving positive feedback regarding the clarity of instructions.
- An Online Appointment Portal: A user-friendly verification process led to higher overall patient engagement, with fewer abandoned sessions and a smoother login experience.
- A Telemedicine Application: Emphasizing visual feedback and clear guidance, this platform achieved enhanced security without sacrificing usability. Patients reported that the process, while unusual at first, quickly became a trusted part of their interactions with the system.
These cases illustrate that when implemented well, a secure verification process is not just a barrier against fraud but also a means to enhance trust and ensure seamless operations. The challenge lies in balancing the fine shades of security with a design that prevents the process from feeling as though it is loaded with tolerance issues or unnecessarily intimidating.
Integrating Security Verification Across the Healthcare Continuum
The integration of robust, interactive verification methods extends beyond just the initial login. Healthcare systems, whether they involve patient portals, mobile health apps, or remote monitoring devices, benefit from continuously reinforced security mechanisms. It is crucial for administrators and developers to consider how these systems work together to create a cohesive network of protections.
Key strategies include:
- Consistent Security Practices: Applying similar verification protocols across different platforms helps patients become familiar with the process, reducing the perceived complexity no matter where they interact with the system.
- Regular Updates and Audits: Cyber threats evolve quickly. Regular audits and system updates ensure that verification methods remain current and effective against emerging risks.
- User Feedback Integration: Collecting and acting on user feedback is essential in adjusting the process. This helps cut through the confusing bits by directly addressing any issues patients might experience.
This unified approach to security verification is key in creating a resilient healthcare network where every touchpoint reinforces the overall protection of sensitive data. By committing to a user-friendly yet secure verification system, healthcare providers can maintain integrity while building a foundation of trust with their patients.
Embracing the Future of Digital Security in Healthcare
The journey toward an optimized secure verification process is ongoing. With rapid advancements in technology, the methods we use today may soon be joined by newer, more sophisticated techniques. Innovations such as blockchain, machine learning, and advanced biometrics are being explored as ways to further enhance the security of healthcare information systems.
Looking forward, several trends are emerging that promise to transform how we think about user verification:
- Blockchain for Data Integrity: By using distributed ledger technology, healthcare providers could secure patient data even further, ensuring that every access request is logged and verified with utmost accuracy.
- Machine Learning and AI: These technologies can be integrated to analyze user behavior patterns in real time, automatically identifying potential threats without inconveniencing legitimate users.
- Context-Aware Security: Future systems may adjust the level of verification required based on contextual factors such as location, device, and recent user activity. This adaptive security model can help strikingly reduce the friction experienced during routine logins.
Each of these advancements brings with it the promise of more secure—and at the same time, smoother—methods for accessing digital health services. The healthcare industry stands at a pivotal moment where technical innovation could lead to remarkable improvements in both security and patient satisfaction. It is critical that these innovations are implemented thoughtfully, with continuous attention paid to the subtle details and little twists that can either enhance or hinder the user experience.
Working Through the Practical Implications for Patient Care
Beyond the realm of technical and digital considerations, the impact of secure verification processes is deeply tied to patient care itself. The ability for patients to quickly and safely access their medical information can have a direct influence on their overall well-being. Easier access means that patients are more likely to monitor their health, adhere to treatment plans, and make informed decisions about their care.
The implications of a well-implemented security verification process are multifold:
- Timely Medical Interventions: When patients can reliably access their data, healthcare professionals can communicate more effectively and respond more rapidly in emergencies.
- Improved Patient Compliance: A user-friendly verification process helps patients adhere to digital communications—which in turn can lead to better compliance with medication schedules and follow-up appointments.
- Empowered Decision Making: Reliable data access fosters an environment where patients are more informed about their health, contributing to a collaborative relationship with their care providers.
Even small enhancements in the way secure verification is implemented can result in meaningful improvements in the overall efficiency and effectiveness of healthcare delivery. By cutting through the tricky parts and handling each verification step with care, our digital systems not only guard against potential breaches but also support the broader mission of modern medicine: to care for and empower patients.
Conclusion: Charting a Path Toward Secure and Accessible Healthcare
In an increasingly digital world, the process of verifying a user’s humanity might seem like a minor technical detail at first glance. However, these interactive security measures are a cornerstone of modern healthcare systems, and their influence stretches far beyond the simple act of “pressing and holding a button until it turns green.”
This op-ed has taken a closer look at the evolving landscape of digital verification in healthcare, exploring the benefits and challenges of these systems from multiple angles. We’ve poked around the intricate world of user engagement, considered the delicate balance between security and usability, and examined how each small twist in the process can have a large impact on patient care and trust.
Whether through advances in biometric technology, behavioral analysis, or adaptive context-aware verification techniques, the future promises a more secure, accessible, and user-friendly approach to healthcare. Healthcare organizations must continue to figure a path that not only addresses the immediate need for protection against cyber threats, but also respects the patient’s journey in a digital environment.
By embracing both the challenges and the opportunities presented by modern security verification methods, we can create an online healthcare ecosystem that values patient safety, fosters trust, and ultimately supports better health outcomes for everyone. As technology evolves and cyber threats become more sophisticated, our approach to digital security must keep pace—ensuring that every patient interaction is protected from start to finish, one green button at a time.
Originally Post From https://medicalxpress.com/news/2025-07-anti-nausea-medication-linked-higher.html
Read more about this topic at
CAPTCHA challenges aren’t accessible, but your website …
How CAPTCHAs work | What does CAPTCHA mean?