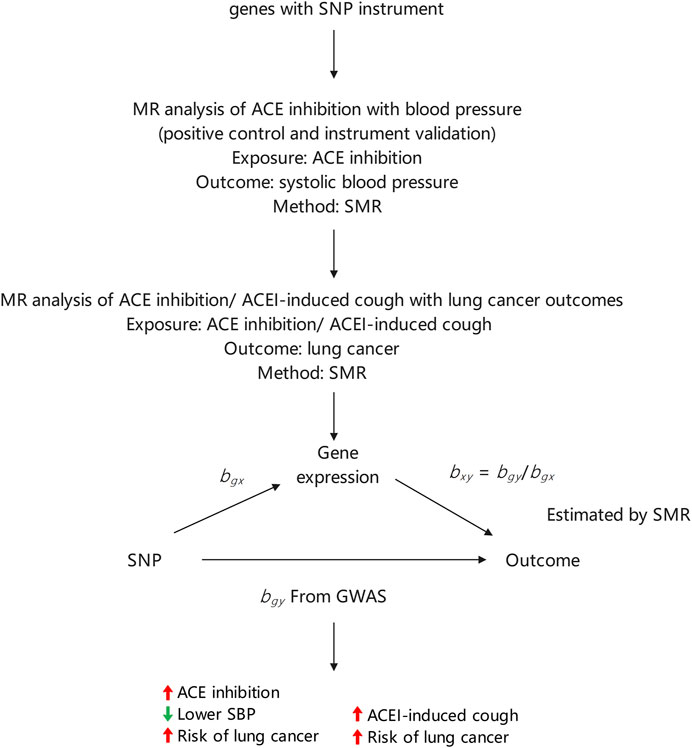
Overview of Online Verification in Healthcare Portals
The modern digital landscape has led many healthcare organizations to incorporate online security measures to protect sensitive patient information. As we increasingly rely on these platforms, the importance of robust security verification processes cannot be overstated. Many users have encountered familiar notifications asking them to “complete security verification” before proceeding. Although this request may seem a bit unusual at first glance, it reflects a broader commitment by healthcare providers to ensure that only genuine human users access their confidential data.
Throughout this editorial, we’ll explore the underlying principles and the reasoning behind these security methods, as well as share opinions on how these processes could be made more user-friendly. The purpose of this discussion is not only to inform but also to encourage improvements in this critical area of digital healthcare. After all, when it comes to safeguarding medical records and personal data, no detail is too small.
Understanding the Verification Process: Pressing and Holding the Safety Button
One of the central components of many online verification systems is the request to “press and hold the button until it turns completely green.” This seemingly simple instruction is packed with meaning and intention. For many users, encountering such a directive can be accompanied by a mix of curiosity and mild anxiety. Is it safe? What might go wrong if I don’t follow the instructions? The answer lies in the design of the verification system itself.
From a technical standpoint, this mechanism is intended to prove that a real person is interacting with the website rather than an automated bot. By requiring the user to press and hold the button, the system can detect subtle variations in pressure, duration, and other little twists of user interaction that automated scripts would struggle to replicate. In essence, this method helps to weed out potentially harmful automated traffic that could compromise the integrity of the system.
While some might view this as a nerve-racking or intimidating step, it is important to realize that these extra measures add an essential layer of security. In healthcare, where the privacy of patient data is paramount, such verification processes are a key component of maintaining trust between providers and patients. Furthermore, these safety protocols help ensure that the data remains confidential and is accessed only by those who are permitted.
User Experience: Examining the Press and Hold Method
One of the most frequent points of discussion in online security verification is the overall user experience. Many users find the process of “press and hold” both novel and somewhat off-putting, especially in the context of a high-stakes environment like healthcare.
For instance, consider the following bullet list that summarizes common concerns users might have about this process:
- Is the button responsive enough on different devices?
- Could the hold duration vary from one browser to another?
- What if I accidentally release the button too soon?
- How do visually impaired users fare with this kind of interactive element?
These concerns are not unfounded. The button’s responsiveness is critical for ensuring that users—especially those who are less tech-savvy—feel comfortable while interacting with the verification system. If the process is perceived as overly complicated or intimidating, patients might abandon the process altogether, potentially delaying crucial access to health information.
The design team behind such systems must balance the need for tight security with a commitment to accessible user interfaces. This dual requirement leads to choices that sometimes seem to present tangled issues or confusing bits, but each decision is often rooted in ensuring the overall safety of the system.
Exploring Alternative Techniques for Online Verification
While the “press and hold” method is gaining traction among various verification systems, it is by no means the only technique available. In recent years, security experts and user experience designers have looked into multiple alternative approaches that could simplify the verification process and reduce any sense of anxiety for end users.
Below is a table summarizing some alternative techniques along with their potential benefits and associated challenges in the context of healthcare portals:
| Verification Technique | Potential Benefits | Associated Challenges |
|---|---|---|
| Image Recognition Captchas |
|
|
| Behavioral Biometrics |
|
|
| Multi-Factor Authentication (MFA) |
|
|
| Press and Hold Verification |
|
|
This table outlines that every method has its own set of tangled issues and twists and turns. It is crucial for healthcare technology designers to strike a balance between offering uncompromised security and maintaining a frictionless interface. As users become more tech-savvy, expectations shift toward smoother workflows that do not inadvertently add stress or discourage access. By comparing these alternative techniques, we begin to notice that the “press and hold” method is often selected for its simple concept, despite its potential drawbacks. It is a refined effort to prove humanity while ensuring that malicious scripts or bots do not infiltrate our healthcare systems.
Making Sense of the Security Alert Message: A Closer Look
At the heart of the security verification process is a direct and clear message that instructs users: “Please complete security verification” followed by the directive to press and hold a button until it turns completely green. This instruction may seem mechanical at first, but it is carefully designed to be both precise and familiar.
Let’s break down the steps to understand the fine points embedded in this message:
- User Prompt: The alert is framed as a polite yet firm instruction. It shows how digital communication can be both courteous and assertive in ensuring safety.
- Visual Feedback: Asking users to press and hold the button until it turns green leverages the power of visual confirmation. The color green, often associated with safety and go-ahead signals, provides the user with a clear indication that the process is being completed correctly.
- Error Handling: In cases where the system detects something amiss, users are advised to contact the support team. This step is critical—not only does it offer a solution for those who may be struggling, but it also instills a sense of reliability and reassurance.
By taking a closer look at these simple instructions, it becomes clear that each detail is engineered to minimize the possibility of error while maximizing trust. That’s not to say that the process is without its confusing bits or that it won’t have off-putting moments for users unaccustomed to such verification steps. However, these instructions represent a necessary compromise between maintaining robust security and ensuring accessibility.
Pressing Concerns: Evaluating User Reactions to Security Verification
Throughout various online forums and patient feedback surveys, a recurring sentiment is that users sometimes feel uneasy about the extra steps required to verify their identity. For many, the need to press and hold a button may seem like an extra hurdle on an already nerve-racking journey when attempting to access important healthcare resources.
Below are some of the key concerns that users have expressed:
- Uncertainty About the Process: Without clear guidance, some users find themselves second-guessing whether they are doing it right, which can lead to frustration.
- Potential Technical Glitches: Issues such as delayed response or variations in button sensitivity across different devices might add to the overall feeling of discomfort.
- Accessibility and Inclusivity: Users with disabilities, including those with limited motor skills, may face additional challenges, making the verification process seem too complicated or intimidating.
- Impersonal Interaction: In a field as personal as healthcare, the seemingly impersonal nature of a security check can sometimes create a barrier between the user and the care provider.
It is essential to recognize that while many of these challenges come across as complicated pieces of design, they are often rooted in the need for enhanced protection. The verification process is not designed to alienate, but to safeguard. That said, health organizations must take the feedback seriously and consider tweaks that could help users feel more at ease—perhaps by offering visual cues, simple instructions, or even alternative verification methods for certain groups of users.
The Intersection of Healthcare Data Protection and Online Verification
There is an undeniable connection between the methods used to secure online platforms and the sanctity of healthcare data. In a world where cyber threats are as unpredictable as they are dangerous, the measures taken to verify user identity are not just technicalities; they act as guardians of personal and medical information.
Healthcare systems use highly critical verification steps as a way of protecting data from automated abuse and cyber attacks. Without these measures, sensitive data—from patient histories and medical records to personal identification information—might fall prey to digital criminals. The complexity of modern cyber security threats demands that healthcare organizations invest in mechanisms that are both thorough and reliable.
While some might view the verification process as just another layer of bureaucracy, opinion leaders argue that it is, in fact, a must-have component of any secure online system. The challenges and confusing bits associated with these security protocols are part and parcel of the evolving battle against increasingly sophisticated online threats. In this context, every extra step taken to ensure the genuineness of a user helps build brighter trust in the system.
Reflections on the Importance of Human Interaction in Security Verification
In an era where automation and artificial intelligence have permeated nearly every facet of our daily lives, the value of human interaction—even in digital form—cannot be underestimated. The reliance on pressing a button, rather than simply ticking a box, serves as a reminder that human input remains an integral part of verifying identity. This simple action reinforces the understanding that there is a human at the other end of the process, a design philosophy that is especially welcoming in sectors like healthcare where personal touch is paramount.
Even though the process might seem like a small, almost trivial step, its implications are significant. When users are asked to interact with a security element in a personal and tactile way, it subtly emphasizes the presence of a thought-out system that values safety. In turn, this fosters confidence among users who might otherwise feel overwhelmed when navigating these digital spaces.
In a study examining patient experiences with online healthcare portals, it was observed that users who were provided with clear, friendly, and human-leaning instructions felt more comfortable and secure. Their responses suggested that these small interactions could alleviate some of the nerve-racking anxiety associated with accessing vital health information.
Taking everything into account, the “press and hold” verification method is more than just a line of text on a screen—it is an affirmation of the commitment to protect personal data and maintain an accessible, respectful relationship with every user. Whether one considers it a trivial bit of design or a critical security measure, its implementation speaks volumes about the intentions behind modern healthcare platforms.
Modernizing Traditional Verification Methods: Looking at the Future
As digital security continues to evolve, so too does the need for more intuitive and responsive verification systems. Opinions among experts suggest that while the current methods, such as the press and hold feature, are effective, there remains significant room for improvement.
Future developments could focus on the following areas:
- User-Centric Design: Creating designs that account for varied user abilities and technological proficiencies can help reduce the off-putting moments experienced by some users.
- Adaptive Verification Methods: Systems might be developed to adjust the verification process based on past user behavior, thus reducing the number of steps for those who have consistently demonstrated secure interaction.
- Integrating Biometrics: Adding layers such as fingerprint or facial recognition could further bolster security, albeit while ensuring that alternative options remain available for users who prefer not to use such methods.
- Seamless Automation: Leveraging the power of artificial intelligence to detect anomalies in user behavior could allow for less intrusive verification processes that still stand up to the threats posed by modern cyber challenges.
These potential developments tie directly into the broader trends seen in many sectors, where personalized and adaptive security protocols are becoming the norm. In digital healthcare environments, the need to protect sensitive data while ensuring a smooth user experience means that careful thought must be given to every little twist in the design process. The key is to avoid overcomplicating the process while still addressing all possible security pitfalls.
The idea is simple: by working through the technical and user experience challenges together, designers can shape a future where security protocols are both effective and pleasantly unintrusive. As healthcare systems continue their shift towards digital solutions, the onus is on developers and UX specialists alike to ensure that every aspect of the process, from initial verification to final data access, is intuitive enough to encourage patient trust and engagement.
Addressing the Technical and Practical Concerns Head-On
While we appreciate the merits of strong verification processes, it is equally important to address the practical concerns from both technical and user perspectives. Let us consider a few of these issues in detail:
Technical Issues and Device Compatibility
One recurring challenge is the variability of device responses. Users may interact with the verification system from various devices—smartphones, tablets, laptops, and desktop computers. Each of these devices may have slight differences in how touch or click commands are processed. This variation can lead to situations where the “press and hold” message becomes a tangled issue. Developers must figure a path to ensure that the process is consistent across all platforms.
For example, one potential solution could be to detect the device type automatically and adjust the required hold duration or button size accordingly. This adaptive mechanism would not only make the process smoother but would also guarantee that no user is left feeling overwhelmed or confused by malfunctioning interactions.
Accessibility for Individuals with Disabilities
An equally important aspect concerns accessibility. A significant portion of healthcare users comprises older adults or individuals with motor skill impairments. For them, even a seemingly small requirement such as holding down a button for a set period might become on edge. It’s essential that the verification process includes alternative methods that allow every patient to complete the security checks without undue stress.
Possible solutions include voice-activated commands or simplified, single-click verification processes for those who may struggle with prolonged pressing. In addition, clear and concise instructions—accompanied by visual aids or audio feedback—could go a long way toward making the process more inclusive. The goal is to work through the subtle parts of design to create a system where every user, regardless of their physical capabilities, feels in control and protected.
User Education and Clear Communication
Another critical area is the role of clear communication in mitigating misunderstandings about the verification process. It is essential to explain why such methods are in place, how they benefit the user, and what steps to follow in case of any issues. By offering a little background on the necessity of these precautions, healthcare providers can help demystify the process and turn what might be seen as an intimidating step into an empowering one.
This could be achieved through:
- Detailed FAQs: Providing answers to common questions about the verification process on the support pages of a healthcare website can eliminate many doubts before they arise.
- Tutorial Videos: Short, engaging videos that walk users through the pressing and holding process can make all the difference for visual learners and those who benefit from guided instruction.
- Live Chat Support: A real-time support option ensures that users who encounter any hurdles have immediate access to assistance, reducing frustration and improving overall trust in the system.
By taking these additional steps, healthcare platforms can significantly enhance user satisfaction. With clear direction and accessible alternatives, even the most intimidating aspects of the verification process can be softened, ensuring that the system remains both secure and friendly.
Balancing Security and Convenience: A Critical Evaluation
As online healthcare continues to expand its digital footprint, providers must walk a fine line between implementing robust security measures and maintaining a seamless and accommodating user experience. The current methods, such as pressing and holding a button, represent one approach to this balance—but like all methods, they have their strengths and their weaknesses.
On one hand, the strict verification protocols are undeniably crucial in protecting sensitive health data. In a landscape that is full of potential cyber threats, disregarding any layer of security could have dire consequences. Yet on the other hand, if the process is too complicated or off-putting, patients might avoid using these digital services altogether, thereby missing out on essential care.
To strike the proper balance, it is important for healthcare technology developers to listen to both security experts and end users. Some of the recommendations for future improvement include:
- A more dynamic interface that adapts to the user’s device and habits.
- Multiple verification options allowing the user to choose the method that best fits their needs.
- Regular reviews of security measures to ensure that they remain effective against emerging threats while providing the simplest possible user experience.
By integrating these ideas within the design framework, healthcare providers can transform the verification process from a nerve-racking requirement into a super important, yet unobtrusive, safety measure. Ultimately, it is about finding that sweet spot where security and convenience work hand in hand.
Learning From Broader Industry Trends and User Feedback
An essential source of insight comes from analyzing trends in other industries. For instance, the banking sector has long been at the forefront of secure online verification, and many of its techniques could be adapted for healthcare applications. Both industries deal with highly sensitive personal data and must confront similar challenges when it comes to distinguishing genuine users from malicious bots.
Comparing the two provides useful parallels: while banks have successfully integrated multi-factor authentication and biometric verification into their systems, some of these concepts could be tailored for healthcare in ways that reduce the intimidating feel of the process. The key lies in careful customization and testing. For example:
- Multi-modal Verification: Allowing users to select from several verification methods—be it press and hold, image recognition, or a quick biometric scan—can cater to a diverse user base.
- Incremental Security Measures: In less critical interactions, a lighter security check might be employed, whereas more sensitive interactions demand more rigorous verification. This gradation makes the process feel less overwhelming in situations where risks are minimal.
- User-Centered Testing: Conducting comprehensive user trials ensures that every new security measure is refined according to real-world feedback. Understanding the fine shades in user behavior helps developers spot the subtle parts where the system might be improved.
By actively learning from the experiences in related fields and incorporating constructive feedback, healthcare platforms can evolve their verification processes to be not only more secure but also more accommodating. In turn, this could lead to greater user engagement and satisfaction, as patients feel both protected and respected.
The Broader Implications: Digital Trust in Healthcare
At the end of the day, the methods employed for online verification have far-reaching implications. Beyond just preventing unauthorized access, these measures play a critical role in building digital trust between healthcare providers and their patients. Trust is not built overnight—it is forged through consistent, reliable, and transparent practices that show users that their privacy is a top priority.
Every time a user completes a security check, it reinforces a subtle but powerful message: this platform cares enough to take the extra steps necessary to secure your personal data. Even if the method might at times seem to have some tangled issues or off-putting steps, the underlying goal is to create an environment that patients can trust with their most sensitive health concerns.
As technology continues to advance and cyber threats become more sophisticated, ensuring digital trust in healthcare becomes even more challenging. The industry must be prepared to re-examine and refine every aspect of its security protocols, adapting to new challenges while maintaining a user-friendly interface. This ongoing process is a testament to the delicate balance of managing your way through complex online systems while keeping patient needs at the forefront.
Conclusion: Looking Ahead With Confidence
In conclusion, the security verification processes—exemplified by the “press and hold until it turns green” system—represent much more than a pesky challenge to overcome. They play a key role in preserving patient privacy, ensuring data integrity, and building trust in the increasingly digital world of healthcare. While these methods may initially seem intimidating or complex, they are a necessary part of a broader strategy to protect individuals from cyber threats.
As we move forward, healthcare systems must find ways to streamline these procedures, addressing the technical and practical challenges while still safeguarding valuable personal data. This might involve adopting alternative verification methods, refining current techniques, or even integrating adaptive systems that evolve in real time based on user feedback. By continuously assessing and improving these methods, the industry can ensure that online healthcare remains both secure and accessible.
Ultimately, the evolution of online verification processes is a reflection of the broader interplay between technology, security, and human experience—a journey full of tricky parts, small distinctions, and subtle shifts in emphasis. By focusing on these areas with thoughtful care and adapting to the feedback of real users, the future of digital healthcare looks promising and secure.
In our ongoing pursuit of a digital healthcare environment that is both safe and easy to use, each tiny improvement builds on the last. It is clear that the path ahead is full of twists and turns, yet by taking a closer look at every element—every press, every hold, every green light—we can create a system that not only protects our data but also strengthens the bond of trust between healthcare providers and the people they serve.
With an eye towards innovation and a commitment to ongoing improvement, healthcare technology can continue to evolve into a model of both excellence and accessibility, ensuring that every interaction, no matter how small, contributes to a safer, more reliable experience for all.
Originally Post From https://medicalxpress.com/news/2025-05-suppressing-key-enzymes-lung-cancer.html
Read more about this topic at
Interactive Security Monitoring
Interactive Application Security Testing (IAST)